Drone detection on your terms
A future-proof drone detection concept, tailored to different risk levels and operational environments
and not all threats are binary

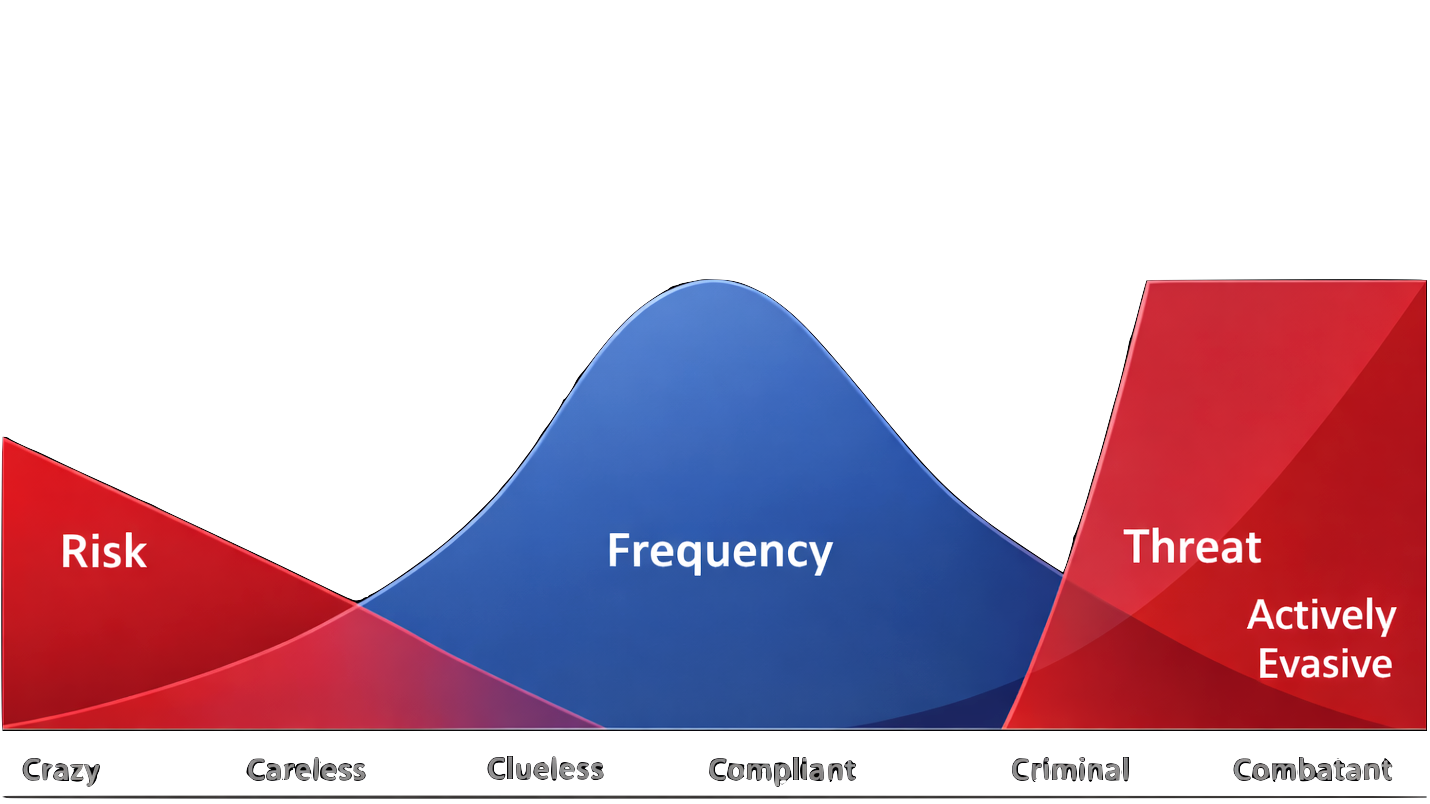
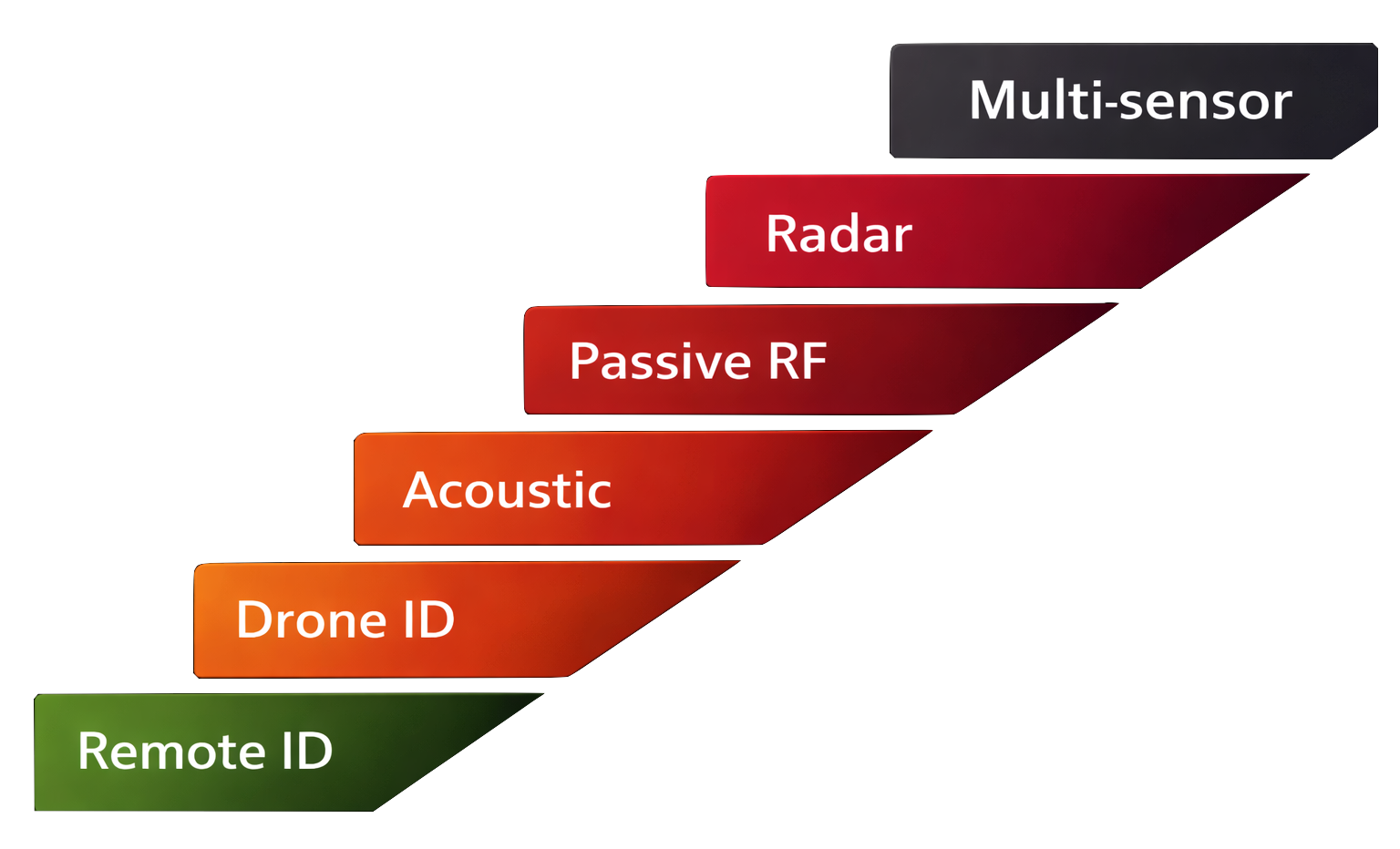
Start at the right level. Scale when needed.
For many organizations, entry-level solutions such as Remote ID and Drone ID deliver immediate value by establishing true situational awareness. As the threat evolves, additional sensors can be added without changing the platform or the operational approach.
This reduces risk, cost, and complexity over time.
↓ Click below on each technology to learn more
Flexible operations. One architecture.
Whether deployed on-premise or hosted by us, the operational model remains the same, allowing systems to evolve over time.
A guide to informed C-UAS decisions
Based on real-world deployments and operational experience, the guide outlines key principles for effective CUAS procurement, from risk assessment to scalable system design.
Download our Whitepaper to learn more →